Banks, NBFCs, and fintech lenders have relied on PDF parsing engines to extract data from customer-submitted bank statements, salary slips, ITRs, and investment proofs.
These parsed insights power critical credit decisions — average balances, EMI outflows, salary credits — forming the backbone of underwriting journeys.
But this dependency has created a glaring vulnerability: when the input document is manipulated, the entire underwriting logic collapses.
Increasing cases of PDF fraud
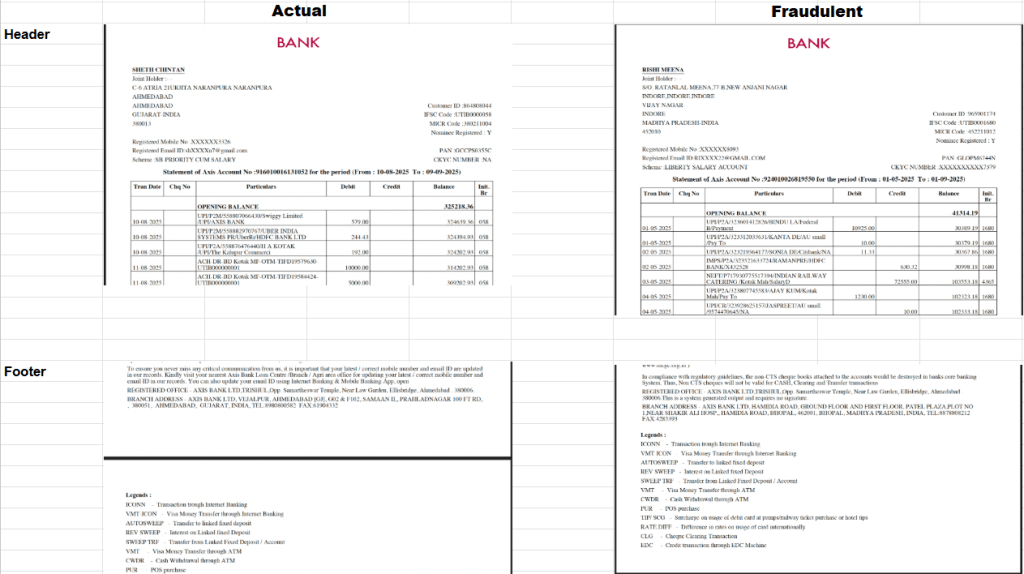
Fraudsters increasingly submit doctored PDFs that visually look perfect and slip past parsing systems.
Common tactics:
- Adding fake salary credits
- Inflating balances
- Removing bounced EMI entries
- Hiding liabilities to improve eligibility
Because these PDFs carry valid-looking metadata and structure, most systems don’t catch them.
If your fraud detection relies on metadata, you’re fighting with a blindfold on.
Why metadata/fingerprinting can’t detect fraud
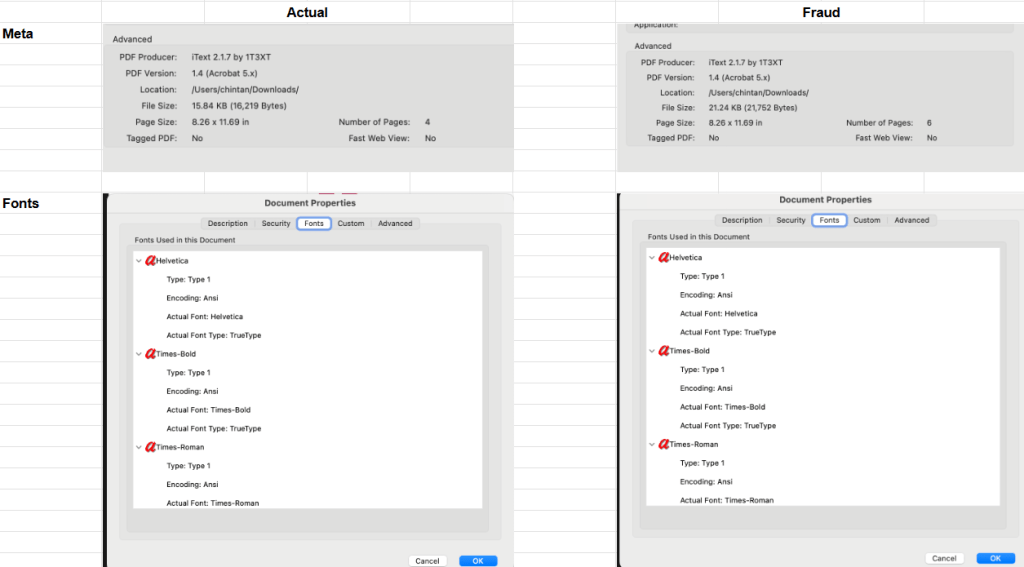
Despite their sophistication, PDFs have no inherent fingerprint to prove authenticity. Here’s why:
Same Software = Same Structure
- Most banks and fraudsters both use iText, the popular open-source PDF library.
- Files from both will have identical object structures and producer tags.
Takeaway: No unique fingerprint exists to distinguish them.
Metadata is user-controlled and over-writable
- Fields like
Producer,Creator,CreationDateare trivially editable. - iText allows fraudsters to copy metadata from real statements.
Takeaway: Metadata can’t be trusted — it’s forgeable in seconds.
No cryptographic integrity in standard PDFs
- PDFs are just containers of text and images.
- They aren’t tamper-proof.
- Only PKI digital signatures can prove origin and integrity.
Takeaway: If it’s not signed, you can’t prove it’s genuine.
Professional tools leave no trace
- GUI editors may leave font mismatches or object residue.
- Libraries like iText regenerate a clean, compliant PDF each time.
Takeaway: Even structural forensics can’t catch this.
Industry reality: why detection always fails
- This isn’t a weakness in your parser — it’s a limitation of the PDF standard.
- Banks that truly care about authenticity don’t rely on parsing or metadata — they use:
- PKI-based digital signatures
- Cryptographic seals
- Secure delivery (portal downloads, SFTP feeds)
Key Point: No tool can detect iText-edited PDFs using only metadata or structure.
Only behaviour can beat forgery (but it’s not enough)
Some lenders try to rely on behavioural checks as a stopgap:
- Look for repeating salaries
- Check for lack of living expenses, ATM withdrawals
- Spot sudden in-and-out balance rotations
While this can catch some frauds, it’s not foolproof. It creates false positives and adds friction to underwriting.
The role of Alternate Data
While PDFs can lie, independent third-party sources rarely do. Triangulating financial behaviour from trusted systems can validate or disprove what a PDF claims:
- EPFO can verify if an employer actually exists and is depositing salaries regularly.
- GST filings reveal actual sales flows for self-employed and business borrowers.
- Credit bureaus help confirm if reported tradelines align with the cashflows being claimed.
This multi-source triangulation adds a strong external lens, but they can’t guarantee authenticity.
The Account Aggregator (AA) way forward
The only scalable, tamper-proof approach is to fetch financial data directly from banks and FIPs using RBI’s Account Aggregator (AA) framework.
AA delivers:
- Bank-stamped, cryptographically signed data
- Zero risk of manipulation
- Consent-driven, auditable flows
- Real-time fetches directly from source systems
If the data doesn’t leave the bank, it can’t be tampered.
Conclusion
Sophisticated PDF frauds are increasingly difficult to detect. No matter how advanced the parser or how many checks are added. As long as lenders depend on PDFs, they will remain exposed to sophisticated fraud.
Account Aggregator is currently the only future-ready solution that sources information directly from banks and stamp it with cryptographic integrity, making authenticity native to every transaction.
Ready to move beyond PDFs?
Secure, signed, real-time bank data is just an AA call away.


